In the ever-evolving landscape of cybersecurity, staying one step ahead of cyber threats is paramount. One concept that plays a crucial role in defending against these threats is "blackholing." In this article, we'll explore what blackholing is, how it works, its significance in the cybersecurity realm, and real-world applications.
Blackholing, in the context of internet security, is a defensive mechanism used to protect networks and systems from malicious traffic or cyberattacks. It operates on the principle of diverting this unwanted and potentially harmful traffic away from its intended target, effectively creating a "black hole" where the data is discarded, rendering it harmless.
How Does Blackholing Work?
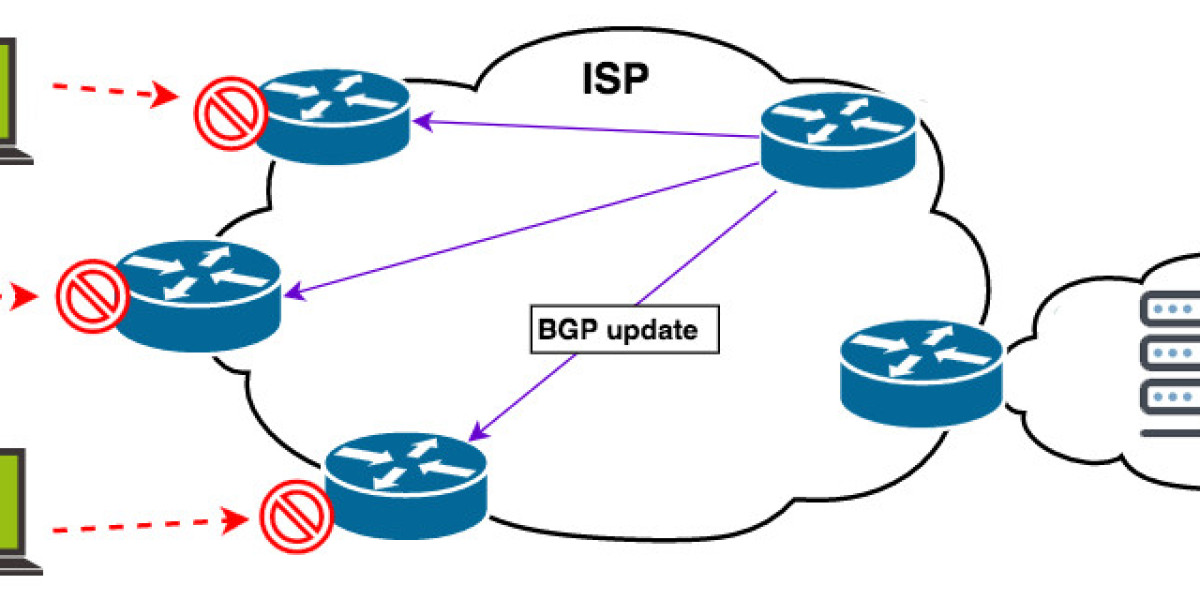
To understand blackholing better, let's delve into the mechanics of internet traffic routing. The Border Gateway Protocol (BGP) is a fundamental component of how data is directed across the internet. It maintains a table of available IP routes and makes decisions on how to send data packets from one network to another.
Blackholing leverages BGP to reroute malicious traffic away from its target destination. When a network detects suspicious or harmful traffic patterns, it can announce a null route for the specific IP address or range associated with the attack. This announcement propagates through BGP, causing routers in the network to direct the malicious traffic towards this null route—a digital dead-end where the data is discarded, preventing it from causing harm.
Types of Blackholing
There are two primary types of blackholing:
- Remote Blackholing: In this form of blackholing, network administrators or service providers take action to mitigate an attack on a remote network. They divert the malicious traffic away from the targeted network, protecting it from harm.
- Local Blackholing: This type of blackholing is employed within a network's own infrastructure to protect its own resources. When a network detects a potential threat from within, it can implement local blackholing to isolate and neutralize the threat.
The Role of Blackholing in DDoS Mitigation
Blackholing is a valuable tool in mitigating Distributed Denial of Service (DDoS) attacks. In a DDoS attack, a large volume of traffic is directed at a target, overwhelming its resources and causing service disruptions. Blackholing can help mitigate such attacks by redirecting the malicious traffic away from the target, allowing legitimate traffic to reach its intended destination.
Pros and Cons of Blackholing
Like any cybersecurity measure, blackholing has its advantages and disadvantages. Some of the pros include its effectiveness in quickly neutralizing threats, its simplicity, and its ability to prevent network congestion during attacks. However, blackholing is not without its drawbacks. It can result in collateral damage, as legitimate traffic may also be diverted, and it may not be a suitable solution for all types of attacks.
Real-World Applications
Blackholing is not just a theoretical concept; it is actively used by internet service providers, data centers, and large organizations worldwide to protect their networks and systems. For example, during a large-scale DDoS attack, a service provider can implement blackholing to safeguard its infrastructure and maintain service availability for its customers.
Conclusion
In the ever-present battle between cyber attackers and defenders, blackholing stands as a valuable tool in the defender's arsenal. It plays a pivotal role in safeguarding networks and systems from malicious traffic and DDoS attacks. However, it is essential to use blackholing judiciously, considering its potential impact on legitimate traffic. As cyber threats continue to evolve, blackholing will remain a vital component of a robust cybersecurity strategy.
FAQs
Is blackholing always an effective way to stop cyberattacks?
Blackholing can be effective in mitigating certain types of attacks, but it may not be suitable for all situations. It is essential to evaluate its appropriateness on a case-by-case basis.
What are the potential drawbacks of using blackholing?
Blackholing can inadvertently block legitimate traffic, causing service disruptions for innocent users. Additionally, it may not be effective against sophisticated attacks that use techniques to evade detection.
Can blackholing be automated to respond to threats in real-time?
Yes, many cybersecurity systems and tools can automate the blackholing process, allowing for swift responses to emerging threats.
Are there alternatives to blackholing for mitigating DDoS attacks?
Yes, there are alternative methods such as rate limiting, traffic filtering, and intrusion detection systems that can complement or replace blackholing in DDoS mitigation strategies.
How can organizations ensure that they don't block legitimate traffic when implementing blackholing?
Careful planning and monitoring are essential. Organizations should use traffic analysis tools and regularly review blackholing policies to minimize the impact on legitimate traffic.